This is an old revision of the document!
Table of Contents
Airdecloak-ng
Description
Airdecloak-ng is a tool that removes wep cloaking from a pcap file. Some WIPS (actually one) actively “prevent” cracking a WEP key by inserting chaff (fake wep frames) in the air to fool aircrack-ng. In some rare cases, cloaking fails and the key can be recovered without removing this chaff. In the cases where the key cannot be recovered, use this tool to filter out chaff.
The program works by reading the input file and selecting packets from a specific network. Each selected packet is put into a list and classified (default status is “unknown”). Filters are then applied (in the order specified by the user) on this list. They will change the status of the packets (unknown, uncloaked, potentially cloaked or cloaked). The order of the filters is really important since each filter will base its analysis amongst other things on the status of the packets and different orders will give different results.
Important requirement: The pcap file needs to have all packets (including beacons and all other “useless” packets) for the analysis (and if possible, prism/radiotap headers).
Usage
Airdecloak-ng 1.4 - (C) 2008-2018 Thomas d'Otreppe
https://aircrack-ng.org
usage: airdecloak-ng [options]
options:
Mandatory:
-i <file> : Input capture file
--ssid <ESSID> : ESSID of the network to filter
or
--bssid <BSSID> : BSSID of the network to filter
Optional:
--filters <filters> : Apply filters (separated by a comma). Filters:
signal: Try to filter based on signal.
duplicate_sn: Remove all duplicate sequence numbers
for both the AP and the client.
duplicate_sn_ap: Remove duplicate sequence number for
the AP only.
duplicate_sn_client: Remove duplicate sequence number for the
client only.
consecutive_sn: Filter based on the fact that IV should
be consecutive (only for AP).
duplicate_iv: Remove all duplicate IV.
signal_dup_consec_sn: Use signal (if available), duplicate and
consecutive sequence number (filtering is
much more precise than using all these
filters one by one).
--null-packets : Assume that null packets can be cloaked.
--disable-base-filter : Do not apply base filter.
--drop-frag : Drop fragmented packets.
--help : Displays this usage screen.
Options
| Option | Param. | Description |
|---|---|---|
| -i | input file | Path to the capture file. |
| –bssid | BSSID | BSSID of the network to filter. |
| –ssid | ESSID | ESSID of the network to filter (not yet implemented). |
| –filters | filters | Apply theses filters in this specific order. They have to be separated by a ','. Example: –filters signal,consecutive_sn |
| –null-packets | - | Assume that null packets can be cloaked (not yet implemented). |
| –disable-base-filter | - | Disable the base filter. |
| –drop-frag | - | Drop all fragmented packets. In most networks, fragmentation is not needed. |
Tests
Capturing traffic
Destroy all VAP (only needed for madwifi-ng):
airmon-ng stop ath0
Create a monitor mode interface (in this case on channel 6):
airmon-ng start wifi0 6
Capture all traffic:
tcpdump -n 65535 -i ath0 -w wep_cloaking_full_speed_dl.pcap
Confirming the key
Trying to crack the WEP key
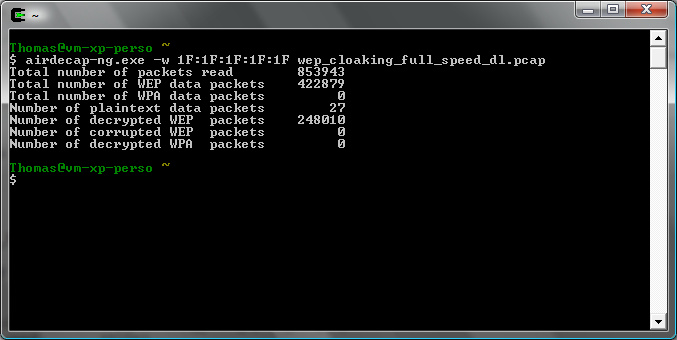
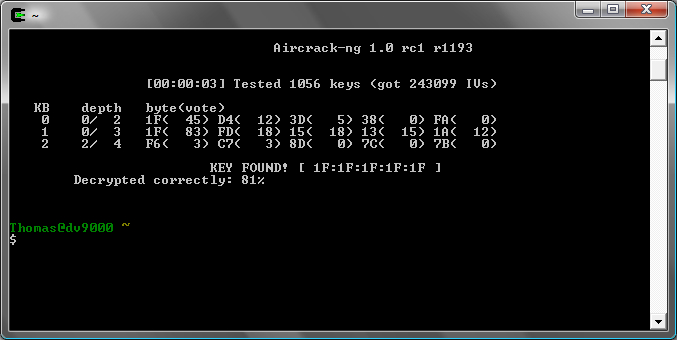
aircrack-ng wep_cloaking_full_speed_dl.pcap -b 00:12:BF:12:32:29 -K -n 64 -d 1F:1F:1F
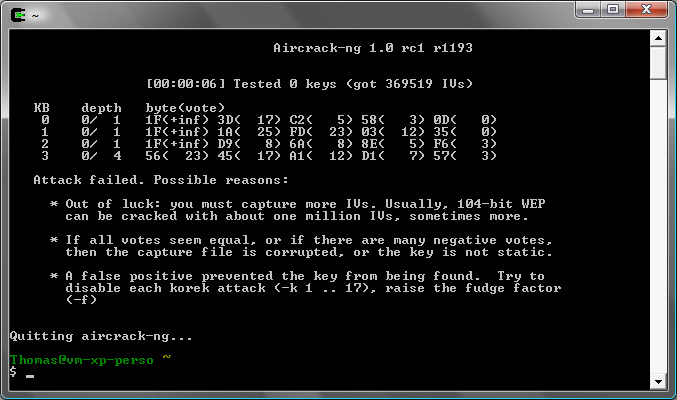
Cracking doesn't work on that file directly even if the beginning of the key is given (-d).
If the whole key is given, cracking it shows that 56% is decrypted correctly and thus 44% of these data packets are cloaked:
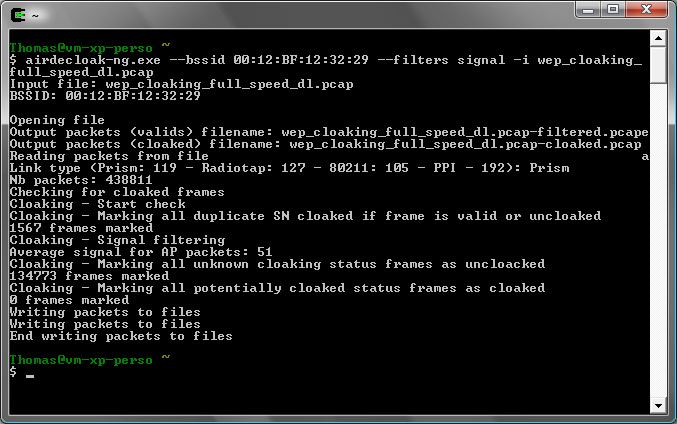
Filtering wep cloaked packets
Base filter and signal filters are applied on this file. It will create 2 files:
- wep_cloaking_full_speed_dl-filtered.pcap: Contains all filtered packets from a specific network.
- wep_cloaking_full_speed_dl-cloaked.pcap: Contains all cloaked packets from this network.
Cracking the filtered capture file
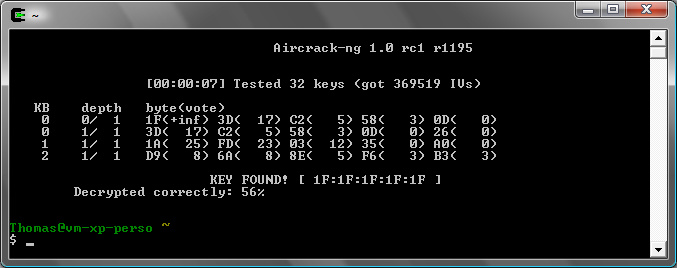
Now cracking it works (PTW doesn't work on this one since it only contains data, nearly no ARP).
Notice “Decrypted correctly: 81%” means that not all packets can be decrypted with the key, so there are still cloaked packets (but not enough to prevent cracking).
Summary
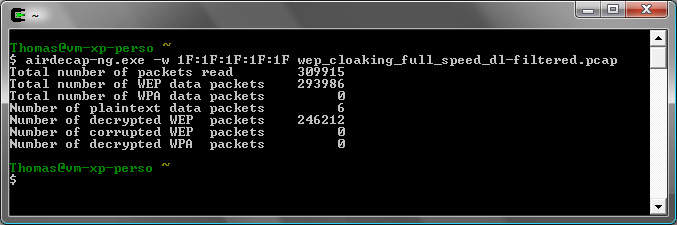
In the filtered file, there's still 293986 WEP data packets and 246212 can be decrypted with the key (that makes 47756 WEP cloaked packets still in the file):
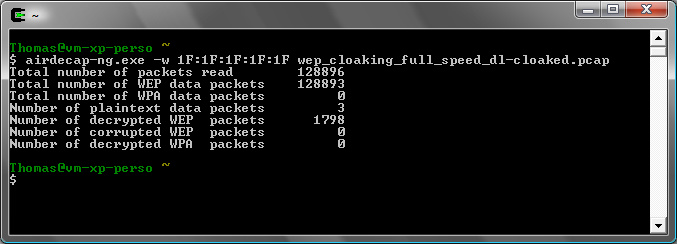
In the file containing the cloaked packets, only a few uncloaked packets are present: 1798 (around 1.4% error).
To sum up, with only one simple filter, around 62% of cloaked packets were removed (126K cloaked in the cloaked packets file + 48K in the filtered file) and it helped cracking the file but we will do better with the other filters and the combined filters.
Wep cloaking
Wep cloaking works by “inserting frames into the air that the attacker thinks are real, and this messes up the statistical analysis of the attacker. (…) The attacker can’t tell the difference between the product frames from the WLAN and the spoofing frames generated (…).”
Wep cloaking is intended to prevent cracking the key, not decrypting the traffic and since nothing is perfect it fails sometimes.
How does it work?
For each Data frame sent by the AP and the clients (even broadcast frames), a cloaked frame is sent by a sensor.
The only difference between the cloaked and uncloaked frame is:
- Sequence number: it uses a different sequences numbers than its uncloaked equivalent (but close to the uncloaked one; sometimes the same).
- WEP parameters
- Content of the payload
- Signal if the sensor is not at the same place as the AP
The other attributes, including the size of the frame is exactly the same.
Drawbacks
Here what was observed when analyzing the technology:
- Since that nearly each packet has its cloaked version in the air, the network speed is reduced: tests show that on a 11Mbit network, with cloaking enabled, the maximum bandwidth is around 300kb/s (and around 600-700kb/sec without).
- Doesn't prevent decrypting the traffic if you have the key, just prevent cracking the key.
- Filtering out cloaked packets is not always necessary to crack the key.
- It takes around 60 seconds for a sensor to “see” the access point and thus during the first 60 seconds of activity of the AP, frames are not cloaked.
Filtering out wep cloaked frames
The following elements can be used to filter out wep cloaked frames:
- Sequence Number (SN)
- Uncloaked frames
- Each data frame is cloaked
- Signal quality
- Initialization Vector (IV)
- Size of the frame
- Other attributes of the frame
- Timing
- Order of arrival
Note: that analysis shouldn't be based on the order of the frame received; the arrival depends on several factors: your location compared to the sensor sending the cloaked frame, the AP, the location of the sensor compared to the AP, and a few other things.
Sequence number
The sequence number is a 12 bit number used in management and data frames. In nearly all cases this number is sequential for each frame sent in one direction; each node (AP or clients) has its own counter for the sequence number.
Uncloaked frames
Management and control frames aren't cloaked, and it seems that only data frames with subtype 0 are cloaked.
Each data frame is cloaked
Each data frame is cloaked but don't count on the fact you'll get all of them or the sensor see them all (it may miss a few depending on its location).
Signal quality
If the AP and sensor are not close to each other, signal quality can be used to filter out cloaked frames.
Initialization vector
This is a 24 bit number. In a capture file, the probability that 2 frames have the same IV is really low; you can safely drop all frames that have the same IV.
Other attributes of the frame
The cloaked frame has the same attributes as “its” uncloaked frame:
- The size of the cloaked frame is the same as the uncloaked
- FromDS and ToDS attributes are the same (logical since the sequence number is the main trick to fool cracking tools).
Size of the frame
Each cloaked frame has the same size as its uncloaked one. Do not filter with only this information because, on a busy network, a lot of frames will have the same size. And even on low traffic networks, sometimes AP sends frames that always have the same size in the air (for example, IGMP frames).
Timing
The time needed to receive a cloaked frame could be analyzed; compared to its uncloaked equivalent since the sensor receives the real frame then forge a wep cloaked frame with the informations of the real one.
For this, 2 packets are needed (one real and one cloaked) and we have to make sure the “cloaking” status of both packets is accurate (and that the cloaked packet is forged against the real one we have).
Remark: The time between each frame recorded may not be accurate.
Order of arrival
Like the “timing” filter, 2 frames (uncloaked and its cloaked equivalent) could be used to find out the cloaked one. When the cloaked one is found, the cloaked frame can be discarded and each 2 frames (going in the same direction; meaning that it has to be done once for the AP and once for each client).
But, like the “timing”, it's not the best filter
Real examples
This part will show real wep cloaking capture files and analyze different possible cases. Filtering is done by combining one or more elements (filters) described above.
Filtering could be done in most cases with the signal and timing (or order of arrival but this is the worst choice) but they should be used as last resort.
Note 2: More examples will be added.
Low traffic network
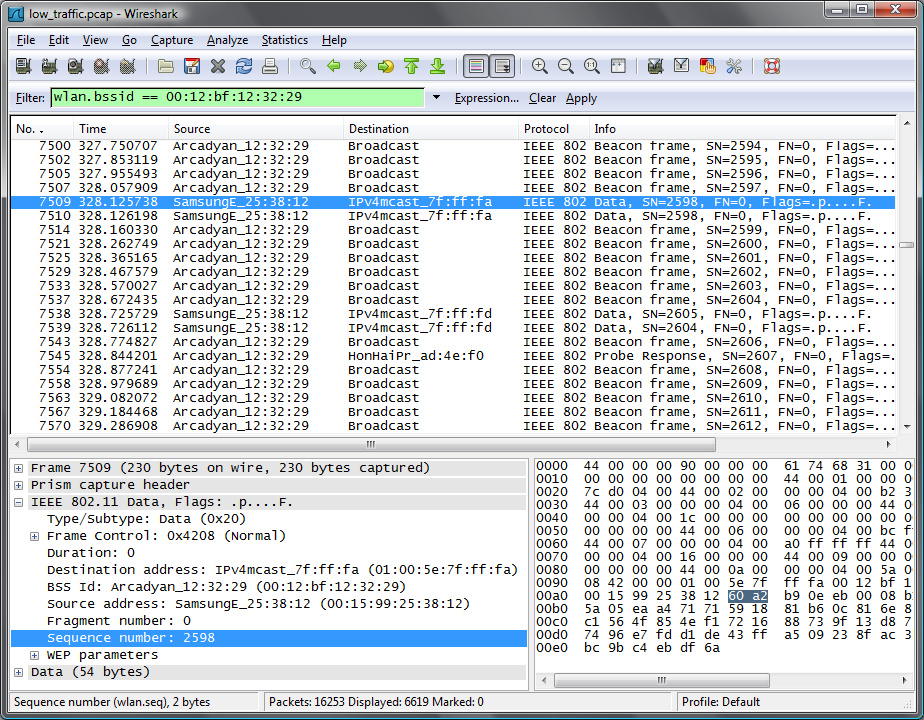
In this example, a computer is pinging another one. This capture is filtered (there's a lot of networks but only one network “has” wep cloaking).
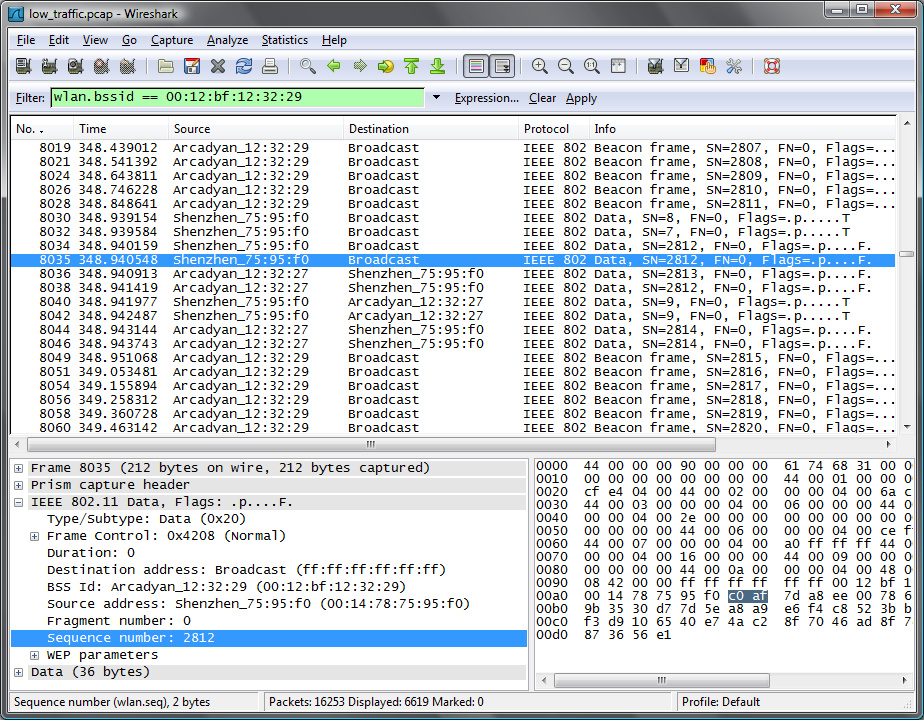
On this pictures, there are 2 real data packets (packet 7509 and 7538), the 2 others are cloaked:
There are a few possibilities to filter out the cloaked packet for 7509/7510: - both packets can be discarded since they have the same sequence number. - use signal/timing to find the cloaked packet.
For packet 7538/7539, it will be easier, it's easy to find out which one is cloaked, a beacon has the same sequence numbers as packet 7539; 7539 is cloaked:
High traffic network
In such network, filtering is more difficult since there's a lot of packets between each beacon. Cloaked packets can still be filtered out by checking beacon sequence number (that's what base filter does).
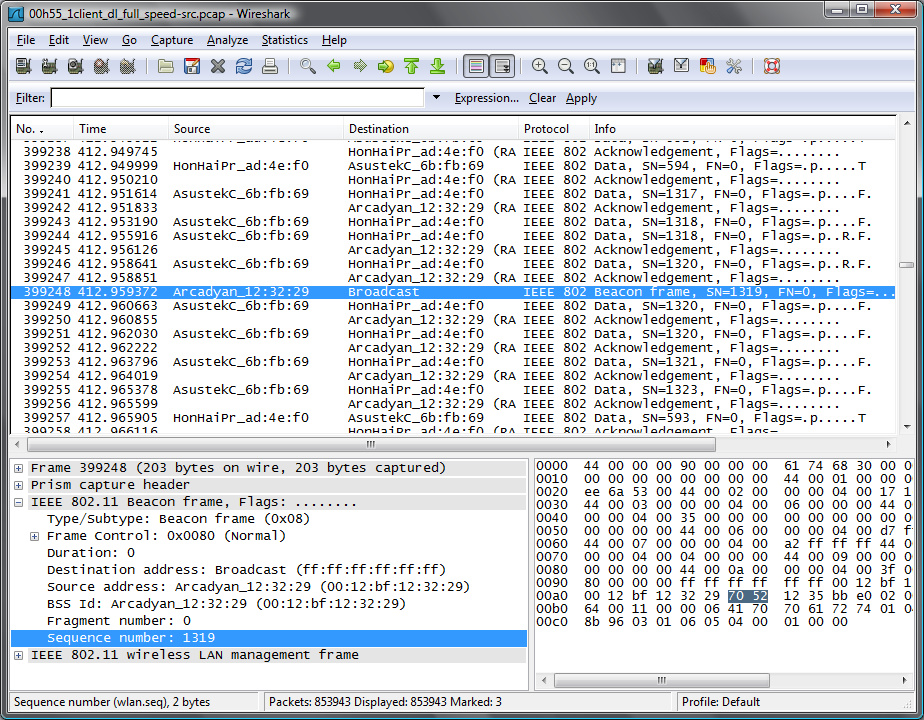
In this case, no packet uses the beacon sequence number …:
… so other ways have to be used. Beacon will still be used but in another way: since 1319 is a valid sequence number, the previous (1318) and the next (1320) sequence numbers of valid packets are known. It's getting more complicated, these sequence number are both used more than once ;)
Since it is known that wep cloaking copies the attributes (including frame size) of its equivalent real frame, wep cloaked packets can be easily found:
| Position | Uncloaked | Cloaked | Frame size | Reason |
|---|---|---|---|---|
| Before beacon | Packet #399244 (SN: 1318) | Packet #399246 (SN: 1320) | 1684 bytes | Arrived before the beacon and thus 1318 is a valid SN. Cloaked has the same attributes as uncloaked; the 2 packets that have the same SN do not have the same attributes |
| Before beacon | Packet #399241 (SN: 1317) | Packet #399243 (SN: 1318) | 1684 bytes | SN 1318 is already used by a valid packet (see previous line) and thus the valid SN before 1318 is 1317 (and also, these 2 packets have the same attributes; that is not the case of the 2 packets that have SN 1318) |
| After beacon | Packet #399249 | Packet #399251 (SN: 1320) | 1400 bytes (SN: 1320) | In this case, there's no good way to distinguish the real from the fake and thus there are 2 choices: discard or use signal filter. That cannot be seen on the picture but the first |
| After beacon | Packet #399253 (SN: 1321) | Packet #399255 (SN: 1323) | 1684 bytes | Sequence number following 1320 (previously valid SN) is 1321, not 1323 |
Implementation
The program uses the following packet statuses:
- unknown: Not sure if it's a real packet or a cloaked one (not yet analyzed).
- uncloaked: Sure that it's not cloaked
- potentially cloaked: It may be a real packet but it could also be a cloaked one, further checks needs to be done to confirm one case or the other
- cloaked: Sure that this packet is cloaked
The main trick of wep cloaking is that it uses sequence numbers close to the real one and thus the central point of our analysis will be sequence numbers.
It also has a few filters that can be combined in a different orders (that will give different results).
Here is how it works:
- Load all the data from a specific network (bssid) into a list
- Mark all data frames as “unknown” status and mark all others (management frames) uncloaked.
- Apply the base filter (see below for more details).
- Apply all (other than base) filters in the order requested by the user (see below for more details).
- Mark of all “unknown” status packets as “uncloaked”
- Mark all “potentially cloaked” frames as “cloaked”
- Write all “uncloaked” frames into one capture file
- Write all “cloaked” frames into another capture file
Note: It is really important to have all frames (and if possible radiotap/prism headers) in the capture file, including the frames “useless” for cracking like beacons, …
Filters
Currently only Base filter and Signal filter are implemented.
Base filter
Since all management frames are not cloaked, any other frame (a few packets away, in the same direction) using the same sequence number is cloaked.
signal
Try to filter based on signal (for packets coming from the AP). Prism or radiotap headers are required for this filter to work.
- Calculate the average signal for all beacons and probe response frames
- Frames that will have the exact same signal will be marked as uncloaked
- Frames that have the potentially cloaked status and have a signal with an absolute difference of more than 2 will be marked as cloaked ( abs(average signal - current frame signal) > 2) ).
- Frames that have the unknown status and have a signal with an absolute difference of more than 3 will be marked as cloaked ( abs(average signal - current frame signal) > 3) ).
Note: Current implementation is based on madwifi-ng signal quality. Note 2: Average signal calculation will be improved. Note 3: Client frames filtering will be added.
duplicate_sn_ap
Remove duplicate sequence number for the AP only (that are close to each other).
duplicate_sn_client
Remove duplicate sequence number for the client only (that are close to each other).
duplicate_sn
Remove all duplicate sequence numbers for both the AP and the client (that are close to each other).
Basically it applies duplicate_sn_ap and duplicate_sn_client filters
consecutive_sn
Filter based on the fact that IV should be consecutive (only for AP).
duplicate_iv
This filter will remove all frames that have the same IV.
signal_dup_consec_sn
Filter using signal (if available), duplicate and consecutive sequence number; it uses all those filters in one and thus filtering is much more accurate (more cases can be covered to find out if packets are cloaked or not).
FAQ
I cannot crack the WEP key, does it mean there's wep cloaking?
If it's a home network, then no. The hardware is too expensive for an individual (it is cheaper to buy new hardware that supports WPA).
Check also the following question.
How can I tell if the data I have comes from a wep cloaked network ?
If you have the following symptoms, there are some chances that the network has wep cloaking:
- The network uses WEP
- Cannot crack the key or “Decrypted correctly” percentage is around 50-65%.
- Using this tool output cloaked packets.
- Some companies advertised on the web that they bought wep cloaking. In this case, google is your friend :).
Are PPI headers supported?
Not yet, but they will.
Why is KoreK used instead of PTW?
Only a few hundred packets in this capture file can be used for PTW and that wasn't enough. See the following entry for more details.
Links
- Defcon 16, Shifting the Focus of WiFi Security: slides, conference and Questions & Answers (will be uploaded)
- Defcon 15, The emperor has no cloak: Conference - Questions & Answers
- Joshua Wright Blog
- Wifisec Mailing list: Perpetuating weak wireless security - Official archive of the mailing list
Thanks
Thanks to Alex Hernandez aka alt3kx from sybsecurity.com for the hardware.